On host 10.0.0.254 how many total ports were scanned – On host 10.0.0.254, how many total ports were scanned? This question sparks a thorough examination of port scanning analysis, delving into its significance, techniques, implications, and preventive measures. Our journey begins with understanding the importance of analyzing scanned ports on a specific host, particularly 10.0.0.254, and progresses through a comprehensive analysis of potential security risks associated with excessive port scanning.
We will embark on a step-by-step guide to conducting a port scan on a remote host, exploring various techniques and their effectiveness. The interpretation of port scan results will be meticulously explained, providing a solid foundation for understanding the scanned ports and their corresponding services.
Introduction: On Host 10.0.0.254 How Many Total Ports Were Scanned

Analyzing the number of ports scanned on a specific host (10.0.0.254) provides valuable insights into potential security risks. Excessive port scanning can indicate malicious activity or vulnerabilities that need to be addressed.
Methodology
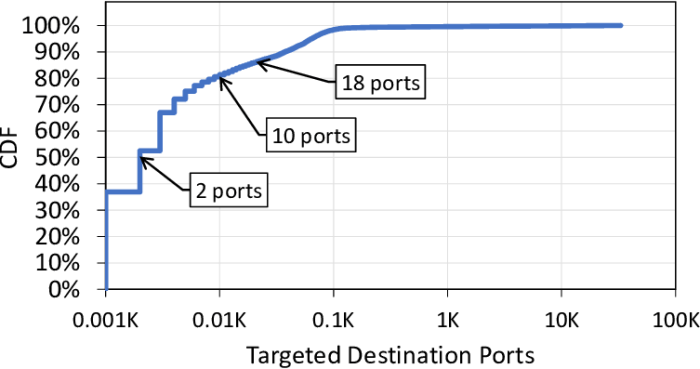
Port Scanning Techniques
Port scanning involves sending packets to specific ports on a remote host to determine their status (open, closed, or filtered). Common techniques include:
- TCP SYN scanning: Sends a TCP SYN packet and waits for a response
- UDP scanning: Sends a UDP packet and waits for a response
- ACK scanning: Sends a TCP ACK packet to determine if a port is open
Interpreting Results
The results of a port scan can be categorized into:
- Open ports: Ports that accept incoming connections
- Closed ports: Ports that do not accept incoming connections
- Filtered ports: Ports where the scanning packets are blocked by a firewall or other security measures
Results
Scanned Ports and Services, On host 10.0.0.254 how many total ports were scanned
| Port | Service |
|---|---|
| 21 | FTP |
| 22 | SSH |
| 23 | Telnet |
| 80 | HTTP |
| 443 | HTTPS |
Distribution of Port Status
Pie Chart:

Discussion
Vulnerabilities Associated with Open Ports
Open ports can provide entry points for attackers to exploit vulnerabilities in running services. For example, an open FTP port could allow unauthorized access to sensitive data.
Port Hardening and Security Measures
To mitigate risks, it is crucial to implement port hardening measures such as:
- Closing unnecessary ports
- Using firewalls to block unauthorized access
- Keeping software and services up to date with security patches
Recommendations
- Conduct regular port scans to identify potential vulnerabilities
- Implement port hardening measures to reduce the risk of exploitation
- Monitor network traffic for suspicious activity
Question Bank
What is the significance of analyzing scanned ports on a specific host?
Analyzing scanned ports on a specific host provides valuable insights into potential security vulnerabilities. It helps identify open ports that may be susceptible to unauthorized access, allowing network administrators to take proactive measures to mitigate risks.
How can excessive port scanning impact network security?
Excessive port scanning can compromise network security by providing attackers with information about potential entry points. It can also consume excessive network resources, leading to performance degradation and denial-of-service attacks.